Part of a blog series from the CoSN’s Cybersecurity Committee in preparation for and tied to Cybersecurity Month.
First, Let’s set the stage for an introduction to NIST.
As part of the U.S. Department of Commerce, the National Institute of Standards and Technology (NIST) promotes innovation by advancing measurement science, standards, and technology. One of the NIST programs is Cybersecurity, which consists of a framework of standards, guidelines, and best practices that help organizations improve cybersecurity risk management. This framework, the NIST Cybersecurity Framework (CSF), offers a widely used approach to help determine and address highest priority cybersecurity risks and develop strategies for improvement.
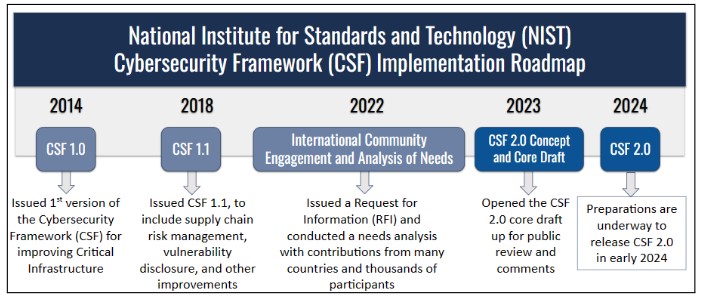
The NIST Cybersecurity Framework isn’t new. It’s been around since 2014. What is new is an overhaul of the framework, the 2.0 version, scheduled to be released in 2024.
What does this mean to us as EdTech Leaders?
We can use the NIST Cybersecurity Framework (NIST CSF 2.0) as a holistic approach at the enterprise level to better manage and reduce cybersecurity risk. The following shows the foundation of the new framework.
- The new CSF 2.0 framework places the highest levels of leadership at the front and center rather than buried down in technology organizations.
- The framework’s common language can be used to improve cybersecurity awareness and communication about the school system’s cybersecurity maturity level from the functional groups to the superintendent and boards of trustees.
- The framework lends itself to determining critical activities and developing strategic plans with quantifiable measures of progress.
- The new CSF 2.0 GOVERN function focuses on how organizations make, fund, and execute decisions regarding cybersecurity.
- Increased focus on collecting metrics about how well the risk management strategy and risk results offer opportunities to reduce the threat landscape while maximizing the return on investment in technology spending.
What Does the New GOVERN Function Include?
The new GOVERN function interlaces cybersecurity, focusing on the people, processes, and technology needed to govern cybersecurity functions within school systems adequately. How? By setting up cybersecurity governance to establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.

Take a Peek At a Few Governance Examples Demonstrating Leadership Commitment
The structure of the new GOVERN function includes a new category for oversight. It moves category objectives from the CSF 1.1 framework in the business environment, risk management, supply chain, and governance up to a leadership level. The following are some highlights.
Organizational Context –The organization’s mission is understood and informs cybersecurity risk management. Internal and external stakeholders are determined, and their needs and expectations regarding cybersecurity risk management are understood. Expectations and legal, regulatory, and contractual requirements surrounding the organization’s cybersecurity risk management decisions are understood.
Risk Management Strategy – The organization’s priorities, constraints, risk tolerance, need statements, and assumptions are established, communicated, and used to support operational risk decisions. Senior leaders agree on cybersecurity objectives and use them for measuring and managing risk and performance. A strategic direction that describes appropriate risk response options is established and communicated. Lines of communication across the organization are established for cybersecurity risks, including risks from suppliers and other third parties.
Cybersecurity Supply Chain Risk Management – Organizational stakeholders identify, establish, manage, monitor, and improve cybersecurity supply chain risk management processes. Policies and procedures require provenance records for all acquired technology products and services. Supply chain security practices are integrated into cybersecurity and enterprise risk management programs, and their performance is monitored throughout the technology product and service life cycle. Leaders require periodic risk reporting about how acquired components are proven untampered and authentic.
Roles, Responsibilities, and Authorities – Cybersecurity roles, responsibilities, and authorities are established and communicated to foster accountability, performance assessment, and continuous improvement. Organizational leadership is responsible and accountable for cybersecurity risk and encourages a risk-aware, ethical, and continually improving culture. Leaders (e.g., directors) agree on their roles and responsibilities in developing, implementing, and assessing the organization’s cybersecurity strategy. The Leader’s expectations are shared, and the cybersecurity risk strategy is monitored.
Policies, Processes, and Procedures – Policies, processes, and procedures for managing cybersecurity risks are established based on organizational context, cybersecurity strategy, and priorities and are communicated and enforced. Personnel must acknowledge the receipt of policies when first hired, annually, and whenever a policy is updated. Policies are updated to reflect changes in technology (e.g., adoption of artificial intelligence) and changes to the business (e.g., acquisition of a new business, new contract requirements).
Oversight – Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy. Measurements are collected about how well the risk management strategy and risk results are helping leaders make decisions and achieve organizational objectives. Key performance indicators (KPIs) are reviewed to ensure that organization-wide policies and procedures achieve goals. Metrics on cybersecurity risk management with senior leadership are collected and communicated.
NIST is accepting comments about the CSF 2.0 through November 4, 2023. If you have suggestions for how to improve the new framework, public comment may be submitted here.
CoSN has many resources available tied to this work: (EDIT)
NIST Crosswalk for K-12 Institutions
Author: Frankie J. Jackson, CETL, RTSBA
Frankie Jackson is a former K-12 CTO of 25+ years, and a Trusted Technology Thought Partner serving K-12 at the State and National Levels. As a former NIST Baldrige Performance Excellence Examiner, CoSN Certified Education Technology Leader (CETL) and instructor, NIST Cybersecurity Practitioner, and Certified Cybersecurity Rubric Evaluator (CCRE), Frankie serves as the Senior Advisor for the Cybersecurity Coalition for Education. Her curriculum vitae is available here.
Date: October 24, 2023
CoSN is vendor neutral and does not endorse products or services. Any mention of a specific solution is for contextual purposes.


